Strengthen industrial cybersecurity without compromising production efficiency
While companies are tapping into the opportunities that the Industrial Internet of Things (IIoT) has to offer, digitalization has become a key initiative for industries. Digitalization has allowed the industrial control system (ICS) landscape to develop quickly in recent years. Originally, ICS networks were physically isolated and almost immune to cyberattacks. However, recently, there has been a rise in the sophistication of cyber attacks, which has prompted everyone from IT to OT personnel to produce solutions that enhance industrial cybersecurity. Thus, understanding industrial cybersecurity requirements will help companies mitigate cybersecurity risks. Read on to learn more.
There are some myths about industrial cybersecurity that may put your facilities and businesses at risk. Watch the video to learn how to debunk the myths and build defense-in-depth security for your industrial networks to ensure continuous operations and the safety of personnel.
There are some myths about industrial cybersecurity that may put your facilities and businesses at risk. Watch the video to learn how to debunk the myths and build defense-in-depth security for your industrial networks to ensure continuous operations and the safety of personnel.
IT  |
OT  |
|
|---|---|---|
| No. 1 Priority | Confidentiality | Availability |
| Focus | Data integrity is key | Control processes cannot tolerate downtime |
| Protection Target | Windows computers, servers | Industrial legacy devices, barcode readers |
| Environmental Conditions | Air-conditioned | Extreme temperatures, vibrations and shocks |
You can use the checklist below to make sure you do not forgot any of the defense-in-depth security measures and select solutions that fit your needs.


To enhance our Device Security, Moxa has identified a big set of cybersecurity features based on the component requirements of IEC 62443. The set of security features have been implemented in a wide portfolio of devices, including Secure Routers, Rackmount Switches, EDS-500E series DIN Rail Switches, select models of Device Sever, and Protocol Gateways.
To prevent network intrusions and attacks, it is essential to have a good access control mechanism in place that can identify, authenticate, and authorize users. Moxa’s network devices support user account management, password policy, and authentication interface management features that meet the technical security requirements of the IEC 62443 standard.
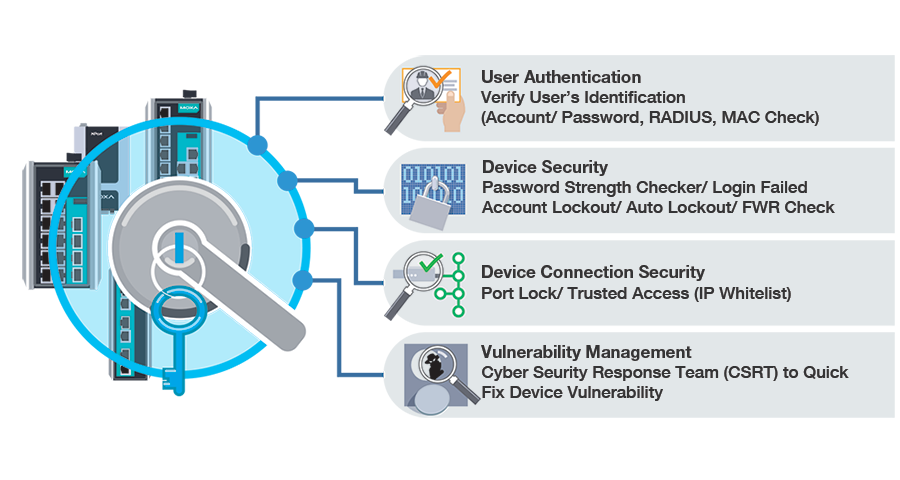

Moxa’s devices support advanced HTTPS/SSH features, which provide a secure channel for data transfer over unsecure networks ensuring reliable processing and retrieval of data. To protect data from being stolen or corrupted, Moxa provides functions such as SNMP password encryption and network configuration encryption, which ensure the highest level of protection for your network devices.
The NPort 6000 secure servers use SSL to implement secure data transmission for Secure TCP Server, Secure TCP Client, Secure Pair Connection, and Secure Real COM modes.. The NPort’s drivers follow the SSL standard and automatically negotiate the encryption key. To prevent hacker attacks, the NPort will automatically switch from DES/3DES to AES encryption for highly secure data transmissions.
Your cybersecurity journey does not end when your network security solution is up and running. You must constantly monitor your networks and audit network events for potential threats. Although it is quite difficult to detect breaches in real time, security event logs can help you identify the source of the issue. Information from these data logs can be used to track network activities, analyze potential threats, or identify devices that are incorrectly configured, which you can then use to disconnect user access, delete user accounts, or restart devices.

As ICS networks keep expanding and more networks continue to converge, it is important to understand the benefits of the defense-in-depth approach when designing security architecture. However, having cybersecurity building blocks deployed in an ICS network is not sufficient to completely protect critical assets from unauthorized access. According to a report published by ICS-CERT, a sound security management model should include the following stages:
Those with malicious intent can still access the secure network if individuals who use the ICS network do not adhere to the security management model. In order to guarantee that the network has not been compromised, check if the ICS network is following the management principles and ensure that all users have read the guidelines to ensure a more secure ICS network.
To prevent unauthorized access to your data and assets, it is essential to have secure access and identity management even for users who are accessing the ICS network from separate sites. It is very important to ensure that only authorized users are the ones accessing the network.
Moxa’s network devices support RADIUS, Role-Based Access Control, web login page alerts, centralized account management, and authentication management. In addition, Moxa also provides WPA2 wireless network security for its wireless devices
Get the Easy-to-Follow Management Guidelines for Critical Infrastructure
No single product, solution, or approach can completely secure an ICS network. Therefore, it is very important to have an understanding of all the network devices and focus efforts on assets that, if disrupted, could have the greatest impact to the organization. Users should start by compiling a network topology to identify which ports can be connected to the network and which should be locked. In addition, the IP access table should be clear to all OT operators in order to prevent users who have not been granted access from connecting to the network.
Moxa offers many Ethernet switches that can be used with sticky MAC addresses in order to significantly enhance security.
Get the Easy-to-Follow Management Guidelines for Critical Infrastructure
Based on the technical recommendations of the IEC 62443 standard, all event logs should be recorded. By having complete event logs, OT operators can trace any cybersecurity incident that occurs on the network and respond to the event in a timely manner. Moreover, network device configuration data should be kept confidential. If the configurations are changed without permission from the network operator, it could result in all of the data being corrupted. Therefore, configuration encryption and regular backups are very important to ensure that the network can return to normal quickly if a cybersecurity incident occurs.
Moxa’s MXview network management software has a job scheduler function, which helps users routinely back up the configuration data and newtork settings. Moxa also provides ABC-02 automatic backup configurators to save the configuration files, which enhances maintenance efficiency and reduces system downtime.

Get the Easy-to-Follow Management Guidelines for Critical Infrastructure

MXview's Security View visualizes the security parameters of your network devices and shows their status on a single page.

MXconfig helps you configure your network to meet established industrial standards in just three steps.

MXview and MXconfig tools help both general industrial users and security experts efficiently manage device security levels on their networks.
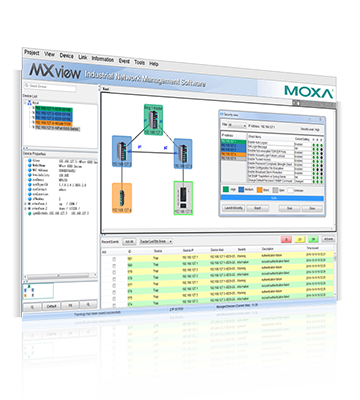
Security Status at a Glance
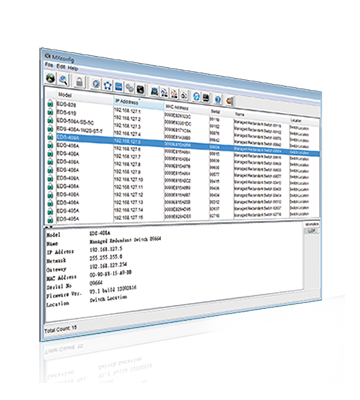
Security Setup in 3 Steps
With over 30 years of experience in industrial networking, Moxa draws on this expertise to help customers build secure networks by offering protection for PLCs, SCADA systems, factory networks, and remote access. Download the case studies to learn more.

Customer: Oil & Gas Service Company
High-capacity oil and gas pipelines are very volatile and often span thousands of kilometers. The pump stations along the pipeline are equipped with analyzers and PLCs. The company found it challenging to maintain a secure and stable network connection between the stations and the remote SCADA system because the PLCs and I/O devices did not have any security features.

Customer: Automotive Parts Plant
An automotive parts plant manager planned to digitalize their production processes. The field devices run on the EtherNet/IP protocol for control unification and data acquisition. As the network infrastructure in this plant is on a large scale, it is very difficult for the plant manager to monitor all devices and visualize the network topologies. In addition, to realize digitization, all networks are interconnected from the field site all the way to the ERP and even to the cloud. It is essential to have good cybersecurity measures to allow this transformation to occur, without compromising production efficiency.

Customer: CNC Machine Builder
Maximizing network uptime enhances machine productivity. Therefore, a leading manufacturer of mechanical power presses needed to provide a timelier and more efficient after-sales service in order to ensure improved machine performance and effective troubleshooting. At first, the machine builder adopted Windows-based Remote Desktop Control (RDC) technology, but security risks and additional costs came at a high price. Furthermore, the Windows-based computer by itself is susceptible to security risks, and the possibility of attacks increases even more when the computer connects to the Internet.
Moxa’s product portfolio is based on the defense-in-depth concept that includes secure devices, secure network infrastructure, and security management.
Moxa takes a proactive approach to protect our products from security vulnerabilities and help our customers better manage security risks.
Moxa has partnered with Trend Micro to respond to the growing security needs of industries as well as the security demands from IT/OT personnel.
MXview provides an integrated management platform that can manage network devices installed on subnets from a web browser at both local and remote sites. In addition, Security View helps users visualize the security status of network devices. By utilizing Security View, network administrators can view the security level of a device, as well as check the security parameters such as the password policy status in real time for each network device. For general industrial users, this view provides built-in user-friendly profiles to meet the technical security requirements of the IEC 62443 standard. Security View also provides security experts the flexibility to create profiles. Network administrators can easily gain a complete overview of the network’s security level and quickly respond to any vulnerability that is identified on their networks.
MXconfig helps users install, configure, and maintain multiple Moxa network devices in just a few clicks. MXconfig’s Security Wizard allows users to select multiple network devices and launch a wizard that can set up or change security-related parameters for those devices. Even though some devices on the network might require complex parameter configurations, network administrators can rest assured that the MXconfig tool will set up each device on their network with the correct configurations.
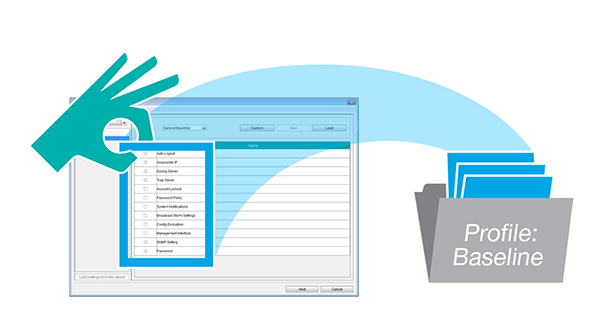
There are multiple security settings for each and every network device that need to be checked and enabled to meet the technical requirements of the IEC 62443 standard. Without the help of tools such as MXview and MXconfig, network administrators have to manually check network devices one by one to set the parameters, which is time consuming and prone to errors. MXconfig’s Security Wizard drastically cuts down on configuration time by supporting batch configuration of large numbers of network devices, which also helps when configuring each device manually.

These devices are Modbus RTU to Modbus TCP gateway converter for 1, 2, & 4 Serial ports. Up to 16 simultaneous Modbus TCP masters are supported, with up to 31 RTU/ASCII slaves per serial port. For RTU/ASCII masters, up to 32 TCP slaves are supported. Standard Modbus network integration, Moxa protocol converter gateway The three standard MGate™ Modbus RTU to Modbus TCP gateway converters (MB3180, MB3280, and MB3480) are designed for easy integration of Modbus RTU to Modbus TCP gateway.. With these models, Modbus serial slave devices can be seamlessly incorporated into an existing Modbus TCP network, and Modbus TCP slaves can be made accessible to serial masters. The MB3180, MB3280, and MB3480 offer features that make network integration easy, customizable, and compatible with almost any Modbus network. High density, cost effective gateway The MGate™ MB3000 Series Modbus RTU to Modbus TCP gateway converters can effectively connect a high density of Modbus nodes to the same network. The MB3280 can manage up to 62 serial slave nodes, and the MB3480 can manage up to 124 serial slave nodes. Each RS-232/422/485 serial port can be configured individually for Modbus RTU or Modbus ASCII operation and for different baudrates, allowing both types of networks to be integrated with Modbus TCP through one Modbus gateway. Auto-Device Routing for Easy Configuration (Patent Pending) Moxa’s Auto-Device Routing function helps eliminate many of the problems and inconveniences encountered by engineers who need to configure large numbers of Modbus devices. A single mouse click is all that’s required to set up a slave ID routing table and configure Modbus gateways to automatically detect Modbus requests from a supervisory control and data acquisition (SCADA) system. By removing the need to manually create the slave ID routing table, the Auto-Device Routing function saves engineers significant time and cost.
The MGate MB3660 (MB3660-8 and MB3660-16) are Modbus RTU to Modbus TCP Gateway, redundant Modbus gateways that convert between the Modbus TCP and Modbus RTU/ASCII protocols. They can be accessed by up to 256 TCP master/client devices, or connect to 128 TCP slave/server devices. The MGate MB3660 series Modbus RTU to Modbus TCP Gateway has isolation models which provides 2 kV isolation protection suitable for power substation applications. The MGate MB3660 gateways are designed to easily integrate Modbus TCP and RTU/ASCII networks. The MGate MB3660 series gateways offer features that make network integration easy, customizable, and compatible with almost any Modbus network. For large-scale Modbus deployments, MGate MB3660 gateways can effectively connect a large number of Modbus nodes to the same network. The MB3660 series can physically manage up to 248 serial slave nodes for 8-port models or 496 serial slave nodes for 16-port models (the Modbus standard only defines Modbus IDs from 1 to 247). Each RS-232/422/485 serial port can be configured individually for Modbus RTU or Modbus ASCII operation and for different baudrates, allowing both types of networks to be integrated with Modbus TCP through one Modbus gateway.
24G-port Layer 2 full Gigabit managed Ethernet switches
Process automation and transportation automation applications combine data, voice, and video, and consequently require high performance and high reliability industrial grade rackmount switches. The IKS-G6524A series full Gigabit backbone switches are equipped with 24 Gigabit Ethernet ports, and support Layer 3 routing functionality to facilitate the deployment of applications across networks, making them ideal for large scale industrial networks. The IKS-G6524A’s full Gigabit capability increases bandwidth to provide high performance and the ability to quickly transfer large amounts of video, voice, and data across a network. The switches support the Turbo Ring, Turbo Chain, and RSTP/STP redundancy protocols, and are fanless and come with an isolated redundant power supply to increase system reliability and the availability of your network backbone.
24+2G/24+4G-port modular managed Ethernet switches
The IKS-6726A/6728A series of industrial rackmount switches are designed to meet the rigorous demands of mission critical applications for industry and business, such as traffic control systems and maritime applications. The IKS-6726A/6728A’s Gigabit and fast Ethernet backbone, redundant ring, and 24/48 VDC or 110/220 VAC ual isolated redundant power supplies increase the reliability of your communications and save on cabling and wiring costs. The modular design of the IKS-6726A/6728A also makes network planning easy, and allows greater flexibility by letting you install up to 4 Gigabit ports and 24 fast Ethernet ports.
The RKS-G4028 Series is designed to meet the rigorous demands of mission-critical applications for industry and business, such as power substation automation systems (IEC 61850-3, IEEE 1613), railway applications (EN 50121-4), and factory automation systems. The RKS-G4028 Series’ Gigabit and Fast Ethernet backbone, redundant ring, and 24 VDC, 48 VDC, or 110/220 VDC/VAC dual isolated redundant power supplies increase the reliability of your communications and save on wiring costs.
The modular design of the RKS-G4028 Series also makes network planning easy, and allows greater flexibility by letting you install up to 28 Gigabit ports with various connector types.
8, 8+3G, 16, 16+3G-port compact modular managed Ethernet switches
The versatile modular design of the compact EDS-600 series Ethernet switch allows users to combine fiber and copper modules to create switch solutions suitable for any automation network. The EDS-600’s modular design lets you install up to 3 Gigabit Ethernet ports and 16 Fast Ethernet ports, and the advanced Turbo Ring and Turbo Chain (recovery time < 20 ms) technology, RSTP/STP, and MSTP helps increase the reliability and availability of your industrial Ethernet network. Models with an extended operating temperature range of -40 to 75°C are also available. The EDS-600 series supports several reliable and intelligent functions, including IEEE 1588 PTPv2, EtherNet/ IP, Modbus/TCP, LLDP, DHCP Option 82, SNMP Inform, QoS, IGMP snooping, VLAN, TACACS+, IEEE 802.1X, HTTPS, SSH, SNMPv3, and more, making the Ethernet switches suitable for any harsh industrial environment.
7+3G-port Gigabit managed Ethernet switches
The EDS-510E is a Industrial grade managed ethernet switch. The Gigabit managed Ethernet switch is designed to meet rigorous mission critical applications, such as factory automation, ITS and process control. The 3 Gigabit Ethernet ports allows great flexibility to build up a Gigabit redundant Turbo Ring and a Gigabit uplink. The switch adopts USB interfaces for switch configuration, system file backup, and firmware upgrade, making it easier to manage.
8G/12G/16G-port full Gigabit managed Ethernet switches
The EDS-G500E series is a Industrial grade managed ethernet switch& is equipped with 8/12/16 Gigabit Ethernet ports and up to 4 fiber optic ports, making it ideal for upgrading an existing network to Gigabit speed or building a new full Gigabit backbone. Gigabit transmission increases bandwidth for higher performance and transfers large amounts of triple-play services across a network quickly. Redundant Ethernet Turbo Ring, Turbo Chain, RSTP/STP, and MSTP increase system reliability and the availability of your network backbone. The EDS-G500E series is designed especially for communication demanding applications, such as video and process monitoring, ITS, and DCS systems, all of which can benefit from a scalable backbone construction.
28G-port Layer 2 full Gigabit modular managed Ethernet switch
The MDS-G4028 Series modular managed ethernet switch supports up to 28 Gigabit ports, including 4 embedded ports, 6 interface module expansion slots, and 2 power module slots to ensure sufficient flexibility for a variety of applications. The highly compact MDS-G4000 Series is designed to meet evolving network requirements, ensuring effortless installation and maintenance, and features a hot-swappable module design that enables you to easily change or add modules without shutting down the switch or interrupting network operations. The multiple Ethernet modules (RJ45, SFP, and PoE+) and power units (24/48 VDC, 110/220 VAC/VDC) provide even greater flexibility as well as suitability for different operating conditions, delivering an adaptive full Gigabit platform that provides the versatility and bandwidth necessary to serve as an Ethernet aggregation/edge switch. Featuring a compact design that fits in confined spaces, multiple mounting methods, and convenient tool-free module installation, the MDS-G4000 Series switches enable versatile and effortless deployment without the need for highly skilled engineers. With multiple industry certifications and a highly durable housing, the MDS-G4000 Series can reliably operate in tough and hazardous environments such as power substations, mining sites, ITS, and oil and gas applications. Support for dual power modules provides redundancy for high reliability and availability while LV and HV power module options offer additional flexibility to accommodate the power requirements of different applications. In addition, the MDS-G4000 Series modular managed ethernet switches features an HTML5–based, user-friendly web interface providing a responsive, smooth user experience across different platforms and browsers. Check MDS-G4012 (12 port modular switch) clicking here & MDS-G4020 (20 ports modular switch) on clicking here
8G+6 2.5GbE-port full Gigabit managed Ethernet switches
The EDS-G4014 Series is equipped with eight Gigabit Ethernet ports and six 2.5 Gbps fiber-optic ports, making it ideal for upgrading an existing network to Gigabit speed or building a new full Gigabit backbone. Gigabit transmission speed increases bandwidth for higher performance and can transfer large amounts of triple-play services across a network quickly. Redundant Ethernet technologies such as Turbo Ring, Turbo Chain, and RSTP/STP increase the reliability of your system and improve the availability of your network backbone. The EDS-G4014 Series is designed specifically for demanding applications such as video and process monitoring, ITS, and DCS systems, all of which can benefit from a scalable backbone. The EDS-G4014 Series is compliant with the IEC 62443-4-2 and IEC 62443-4-1 Industrial Cybersecurity certifications, which cover both product security and secure development life-cycle requirements, helping our customers meet the compliance requirements of secure industrial network design.
Railway 1, 2, and 4-port RS-232/422/485 serial device servers
The NPort 5000AI-M12 is a Serial to Ethernet Module, designed to make serial devices network-ready in an instant, and provides direct access to serial devices from anywhere on the network. Moreover, the NPort 5000AI-M12 is compliant with EN 50121-4 and mandatory sections of EN 50155, covering operating temperature, power input voltage, surge, ESD, and vibration, making them suitable for rolling stock and wayside applications where high levels of vibration exist in the operating environment.
1-port RS-232/422/485 serial device servers
The NPort® 5100A device servers are worlds most popular Serial to Ethernet Gateways, designed to make serial devices network-ready in an instant and give your PC software direct access to serial devices from anywhere on the network. The NPort® 5100A device servers are ultra-lean, ruggedized, and user-friendly, making simple and reliable serial-to-Ethernet solutions possible. A Greener Serial-to-Ethernet Solution
The MiiNe is a small but powerful Arm-based serial-to-Ethernet SoC with RAM and Flash embedded. With the MiiNe inside, the NPort® 5110A Series’ power consumption is less than 1 W. The NPort® 5100A Series saves at least 50% on power consumption compared to existing solutions on the market, helping engineers meet the tough environmental compliance challenges found in today’s industrial environments.
1-port RS-232 / 422 / 485 serial device server.
NPort 5100 series device servers (serial to ethernet converters) are designed to make serial devices network-ready in an instant. The small size of the servers makes them ideal for connecting serial devices such as card readers and payment terminals where connections are RS-232 & devices like PLC’s, Energy meters where Serial ports are RS-422 or RS-485, to an IP-based Ethernet LAN. Use the NPort 5100 series device servers to give your PC software direct access to serial devices from anywhere on the network. Using serial to ethernet converters to connect legacy serial devices to Ethernet is now common, and users expect device servers to be cost-effective and to provide a broad selection of useful functions. With its full support of Microsoft and Linux operating systems, the NPort 5110 provides the best choice for serial (RS-232)-to-Ethernet converters. For RS-485 port or a combo – RS-232 / 422 / 485 ports, please use our Nport 5130 or Nport 5150 models!
2-port RS-232/422/485 serial device servers
The NPort 5200 serial to ethernet device servers are designed to make your industrial serial devices Internet-ready in no time. The compact size of NPort 5200 serial device servers makes them the ideal choice for connecting your RS-232 (NPort 5210/5230/5210-T/5230-T) or RS-422/485 (NPort 5230/5232/5232I/5230-T/5232-T/5232I-T) serial devices—such as PLCs, meters, and sensors—to an IP-based Ethernet LAN, making it possible for your software to access serial devices from anywhere over a local LAN or the Internet. The NPort 5200 Series has a number of useful features, including standard TCP/IP protocols and choice of operation modes, Real COM/TTY drivers for existing software, and remote control of serial devices with TCP/IP or traditional COM/TTY Port.
8 and 16-port RS-232/422/485 terminal servers with dual-LAN redundancy
The CN2600 has two separate LAN ports that can be connected to separate LAN networks. Dual-LAN redundancy involves setting up two separate physical networks to connect the PC host with the CN2600 (the PC host also requires two LAN cards). If one connection fails, the PC host can still communicate with your serial devices over the alternative LAN connection.
8 and 16-port RS-232 terminal servers
The CN2510 provides an easy console management solution in a convenient 1U rackmount package. With its RS-232 ports, connections are easily established to the console ports of network equipment, such as Unix servers or routers, for centralized management of the attached devices. Each device’s RS-232 console port becomes a network-accessible node, giving users Telnet access from anywhere on the network for configuration and management of the device. Full modem control signals are supported, ensuring compatibility with a wide range of serial peripherals.
8/16/32-port RS-232/422/485 rackmount secure terminal servers
The NPort® 6600 series of secure device servers is the right choice for applications that use large numbers of serial devices packed into a small space. Security breaches are intolerable and the NPort® 6600 ensures data transmission integrity with support of DES, 3DES, and AES encryption algorithms. Serial devices of any type can be connected to the NPort® 6600, and each serial port on the NPort® can be configured independently for RS-232, RS-422, or RS-485 transmission.
4-port RS-232/422/485 secure terminal servers
The NPort® 6450 is a 4-port device server that uses the SSL and SSH protocols to transmit encrypted serial data over Ethernet. Up to 4 serial devices of any type can be connected to the NPort® 6450, with all four devices using the same IP address. The Ethernet port can be configured for a normal or secure TCP/IP connection.
2-port RS-232/422/485 secure terminal servers
The 2-port NPort® 6250 device servers use the SSL and SSH protocols to transmit encrypted serial data over Ethernet. Models are available for connecting to a 10/100BaseT(X) copper Ethernet or 100BaseT(X) fiber network. Both single-mode and multi-mode fiber are supported.
1-port RS-232/422/485 secure terminal servers
The NPort® 6150 1-port device servers use the SSL and SSH protocols to transmit encrypted serial data over Ethernet. The NPort® 6150’s 3-in-1 serial port supports RS-232, RS-422, and RS-485, with the interface selected from an easy-to-access configuration menu.